Solaris Administration
Tech. Bulletin
How to add Network Address Translation to Firewall-1 and Solaris 2.X
Trevor Paquette
Senior Unix Network Architect
![]()
Table of Contents
Introduction
What is this document about?
OVERVIEW
1.0 Get the IP address of the system that you want to NAT (Internal IP)
2.0 Get the IP address of the system as it should be seen (External IP)
3.0 Add routing statement
4.0 Add ARP statement
5.0 Add Firewall-1 objects and NAT rules
6.0 Save and recompile the firewall rules
This document describes how to setup CheckPoint Firewall-1 3.X and Solaris 2.X to do Network Address Translation (NAT) for an IP address in a one-to-one mode (also known as static translation)
NAT is used to hide or mask an IP address from one or more networks.
Now that you have decided that you would like to do NAT, you will have to perform the following functions:
Each of the stages outlined above must be done one at a time.
Commands to enter will be in boldface italic font, where applicable.
Responses from the system will be in plain italic font, where applicable.
Let’s say that the following diagram is what we want to achieve.
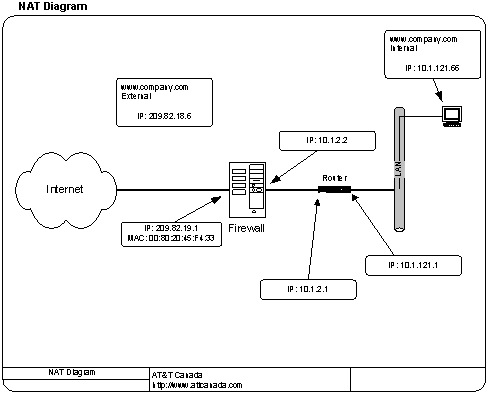
We want to make the web server at IP address 10.1.121.66 appear as 209.82.18.6 on the other side of the firewall. Following the steps outlined above, we can easily do this in under 5 minutes. (
This assumes that all routing to the external and internal subnets are already in place)
Get the IP address of the system that you want to NAT (Internal IP)
From the diagram this is 10.1.121.66
From the diagram this is 209.82.18.6
We need to tell the firewall which way to send packets meant for the web server. This is where a lot of folks get confused. Even though the firewall NATs all of the traffic, we still need to tell the system that the external IP address is to be routed through the internal router. We do this by added the following line to the system boot scripts (
We (AT&T) put the routing and ARP statements in /etc/rc3.d/S99rc.local We do this so we are not mucking up the system startup scripts) :route add host 209.82.18.6 10.1.2.1 1
You can also type that command directly on the command line to have it take effect right away. What does this actually do? This tells the system that the IP address 209.82.18.6 is to be routed though the router located at 10.1.2.1. This is the right way for this traffic to go.
Now if we enter
netstat –nr | grep 209.82.18.6
we should see a line that looks like:
209.82.18.6 10.1.2.1 UGH 0 0
We know that the route has been added successfully.
Now we have to tell the system that it will be answering for 209.86.18.6. This is the part that most folks forget to add. We need to make the external NIC responsible for picking up packets destined for the external IP address. We need to add an ARP entry for the external IP address with the MAC address of the external NIC. We do this by adding the following line to the system boot scripts:
arp –s 209.82.18.6 00:80:20:45:F4:33 pub
Again, you can also type that command directly on the command line to have it take effect right away. Now if we enter
arp –a
We should see a line that looks like:
hme0 209.82.18.6 255.255.255.255 SP 00:80:20:45:f4:33
hme0 is the NIC that has the MAC address listed.
Now that the system is ready, we have to tell Firewall-1 what to do. We do this by first creating the internal and external objects. We need to create two new ‘Workstation’ objects.
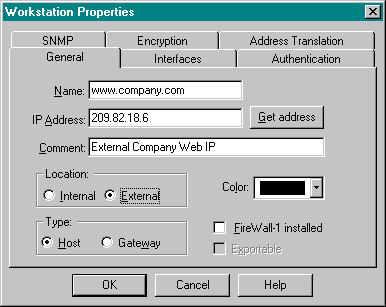
The first object is the ‘External’ IP, how it is known to the outside world. We use this as the ‘official’ name ‘www.company.com’.
You can enter the information as shown below:
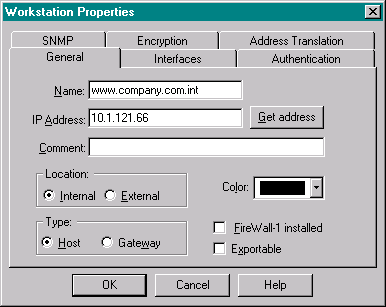
The next object is the ‘Internal’ IP, how the inside network knows it. We use this as ‘www.company.com.int’. You can enter the information as shown below.
Now that we have created the two objects, we need to setup FW-1 to do the actual NAT. Go to the Address Translation Tab and enter the following:
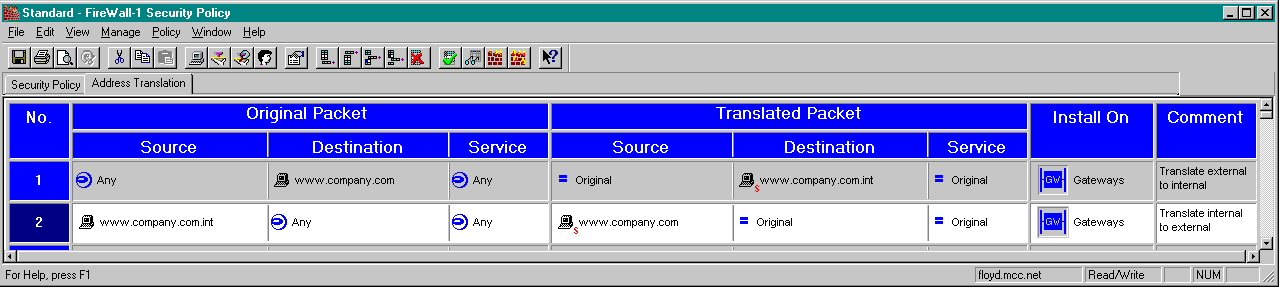
This sets up FW-1 to do the actual translation.
One tip that I have found, in your actual rulebase where you want to deal with these new objects, you will probably have to enter BOTH objects each time you want to put it into a rule. I have found that unless I do this, the traffic gets rejected.
Your rules that use these new objects should looks like this:
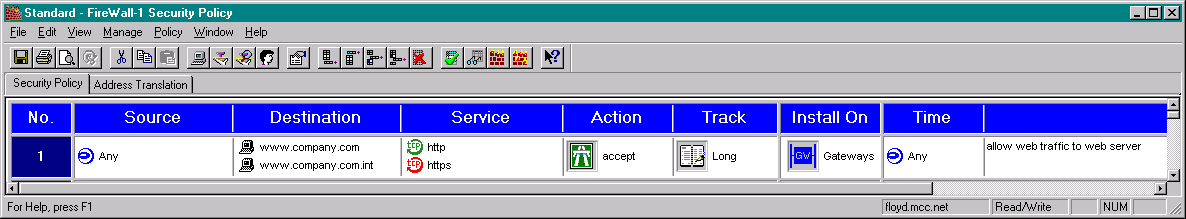
The last step is to now save and recompile the rules.
Congrats.. You’re done.