Essential Check Point FireWall-1 Errata
It's harder to fix stuff printed on dead trees than it is to fix web pages. The following is a list of things where I either screwed up initially or changed since I originally wrote it and needs updating to reflect it. If you spot anything not on this list, send an email to [email protected]. Each error listed here also says which printing of the book fixed it, if any, so you may be lucky enough not to see any of these errors. :-)
p. 36: In the block where I talk about adding licenses, replace fw putkey with fw putlic. This is fixed in the third printing.
p. 59: In the block where I talk about location, replace UPN-1 with VPN-1. This is fixed in the third printing.
p.68: I could use better words in the second paragraph under the Anti-Spoofing heading. Here's some revised ones:
For example, if valid address is 192.168.182.0/24 and the interface is le0:
- Packet with source IP address 192.168.182.4 can come into le0.
- Packet with source IP address 192.168.1.8 cannot come into le0.
- Packet with destination IP address 192.168.182.4 can be routed out le0.
- Packet with destination IP address 10.0.0.4 cannot be routed out le0.
This is fixed in the third printing.
p. 78: Figure 4-22 should have a "no" going off the "Does packet pass anti-spoofing checks?" block to the "drop or reject" packet block. This is fixed in the third printing.p. 89: In the block where I talk about rule x hides/conflicts with rule y for services z, replace occurrences of HTTP with SSH. This if fixed in the third printing.
p.117:
The fw logswitch command to rotate the logs at 11:59pm in Unix/IPSO should be:
I also screwed this up on NT as well. The command should be:59 23 * * * /etc/fw/bin/fw logswitch > /dev/null 2>&1
at 11:59pm /every:m,t,w,th,f,s,su %FWDIR%\bin\fw logswitch
This is fixed in the third printing.
p.176:
In this paragraph, I used 'sir-robin' when I meant to use sir-lancelot. The corrected paragraph should read
To illustrate the way these options work, let's use the users sir-gallahad and sir-lancelot with the rule created earlier. The allowed sources and destinations for sir-gallahad are both any. The allowed sources for sir-lancelot are any, but his allowed destination does not include castle-anthrax (i.e., it is not "any" or a group that includes castle-anthrax). If the User Authentication properties for the rule were defined using "intersect with user database" for the destination, then when sir-lancelot tried to authenticate to access castle-anthrax, he would be denied, even if he were coming from camelot and presented correct authentication. If the setting were "ignore user database," sir-lancelot would be permitted to go to castle-anthrax provided he supplied the correct authentication and were coming from camelot.
This is fixed in the second printing.
p.245:
:ftp_allowed_cmds is missing a colon in front of it. This is fixed in the second printing.
p.282: In the second note, the Microsoft Article ID is Q282312, not Q82312. This is fixed in the second printing.
p.297: The third entry from the bottom in table 9-5 needs to be corrected as follows:
Expression: tcp[13] \& 0x12 != 0
Description: Show only TCP SYN/ACK packets, tcp[13] refers to the 13th byte in the TCP header of the packet (the \ before the ampersand is to escape it for the shell).
This is fixed in the third printing.
p.298: The fourth entry from the top in table 9-7 needs correcting. "icmp" should be in lower case as "Icmp" in uppercase is incorrect. This is fixed in the third printing.
p.307: Figure 9-14 is wrong. It should be this: ( hi-res version for printing)
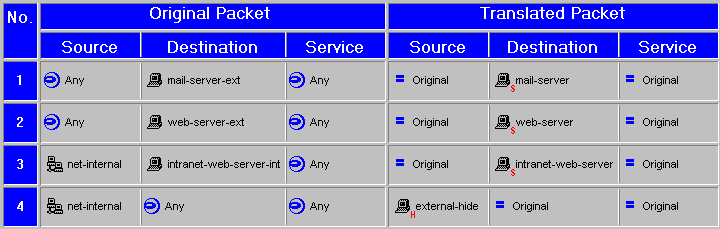
This is fixed in the third printing.
p.315: The first sentence on this page uses the word
"encrypt" when I meant to use "decrypt." The last part of the sentence should
read: ... and only the destination node can decrypt it. This is fixed in
the third printing.
p.324: The first sentence under the "Supports Aggressive Mode" heading, the word "instead" is used twice in the first sentence. The second instance of the word should be stricken (i.e. the sentence should end with "used"). This is fixed in the third printing.
p.422: The correct URL for Foundry Networks is www.foundrynet.com. This is fixed in the third printing.
p.469-488: The
firewall-1.conf and
firewall1.schema files have changed per the links. I have updated these
files to support both 4.1 and NG. This is fixed in the third printing.
p.496-497:
Replace occurrences of "fwhmem?Wa00000" with "fwhmem?W0xa00000" . This is fixed in the second printing.
p.498:
I've found an easier way to accomplish modifying fwhmem on Linux, thanks to an email from Check Point.
On Linux, modify the file $FWDIR/boot/modules/fwkern.conf. Add the following line to the file:
fwhmem=0xa00000You will need to restart FireWall-1 for this change to take effect.
This is fixed in the second printing.

